[Last updated 9/7/2025]
DMARC: Understanding and Why it is needed.
At KartHost, we’re all about empowering you to manage your email with confidence. If you’re sending emails from your domain or forwarding them to another address, you’ve probably come across terms like SPF, DKIM, and DMARC. These tools work together to secure your email, prevent spam along with phishing, and ensure your messages land in inboxes. So, what are they and why are they important to you?
What are SPF, DKIM, and DMARC?
Picture SPF, DKIM, and DMARC as your email’s security squad, verifying that your messages are legitimate and protecting your domain from misuse by scammers or otherwise.
Here’s what each does:
SPF (Sender Policy Framework): SPF acts like a guest list, telling receiving email servers which servers or IP addresses are allowed to send emails for your domain. For example, if you use KartHost’s email servers, SPF ensures only those servers can send emails from your domain, stopping spammers from faking your identity.
DKIM (DomainKeys Identified Mail): DKIM adds a digital signature to your emails, like a tamper-proof seal on an envelope. This signature confirms the email came from your domain and hasn’t been altered, proving its authenticity.
DMARC (Domain-based Message Authentication, Reporting, and Conformance): DMARC is the leader of the pack. It uses SPF and DKIM to create a policy that tells receiving servers what to do with emails that fail authentication checks (e.g., mark as spam or reject). DMARC also provides reports to help you monitor all emails sent from your domain and its sub-domains, giving you full visibility into your email activity.
What Does DMARC Actually Do?
If an email fails both SPF and DKIM checks, DMARC tells the email provider what to do based on the setting it is in:
- p=none: Just report the failure, don’t block the message.
- p=quarantine: Send the suspicious message to the spam/junk folder.
- p=reject: Block the message completely.
Understanding a DMARC Record
|
Tag |
Value |
What It Means |
|
v |
DMARC1 |
DMARC version (always DMARC1) |
|
p |
none/quarantine/reject |
Policy for mail failing DMARC |
|
rua |
mailto:your-report@example.com |
Where to send daily summary (aggregate) reports |
|
ruf |
mailto:your-forensic@example.com |
Where to send detailed (forensic) reports (if supported) |
|
fo |
1 |
Request forensic reports for any SPF or DKIM failure. (you will receive a forensic failure report whenever either SPF or DKIM fails to align) |
Who Sends DMARC Reports and When?
- You do not control when DMARC reports are sent.
- Reports are sent by the email providers (like Google, Microsoft, Yahoo) who receive mail from your domain.
- Most providers send reports once every 24 hours.
These tools ensure your emails are trusted, reduce spam and phishing risks, and keep your domain’s reputation intact.
Why DMARC Is a Game-Changer
DMARC is especially important because it’s becoming a must-have for email senders. Here’s why it matters and what you need to know:
Covers All Emails and Sub-Domains: DMARC applies to every email sent from your domain and any sub-domains (e.g., newsletter.yourdomain.com). This ensures comprehensive protection, whether you’re sending marketing emails, personal messages, or forwarding emails to another account.
Required by Major Providers: Companies like Google, Yahoo, and Microsoft now require DMARC for domains sending high volumes of email (typically over 5,000 emails per day to their servers). If you exceed this threshold without a proper DMARC policy, your emails may be flagged as spam or rejected outright, meaning your messages might not reach Gmail, Yahoo Mail, or Outlook inboxes.
Consequences of Ignoring DMARC: Without DMARC, your domain is vulnerable to spoofing, where spammers send fake emails pretending to be you. This can damage your brand’s reputation and trick recipients into sharing sensitive information. For high-volume senders, ignoring DMARC risks emails being blocked by major providers, hurting your ability to communicate with customers or contacts.
Testing with p=none: DMARC’s p=none policy is perfect for getting started. It lets you monitor email activity without affecting delivery. DMARC reports will show you which emails pass SPF and DKIM checks (authenticated) and which fail (potentially unauthorized). This helps you identify issues, like misconfigured servers or spammers using your domain, before enforcing stricter policies like p=quarantine (send to spam) or p=reject (block entirely). It is important to note that you should treat this as a temporary test setting rather than a permanent setting to sit in.
Setting Up SPF, DKIM, and DMARC
Whether you’re sending emails through KartHost’s servers or forwarding them to another address, setting up these tools is manageable with your domain’s DNS settings. Here’s how:
SPF Setup:
- Add a TXT record to your domain’s DNS to list authorized email servers.
- Example: v=spf1 include:karthost.com-all
- This allows only specified servers (like KartHost’s) to send emails for your domain. The -all rejects unauthorized senders.
DKIM Setup:
- Add a TXT record with a DKIM public key, provided in your KartHost Customer Center.
- Example: selector._domainkey IN TXT "v=DKIM1; k=rsa; p=[your-public-key]"
- This lets receiving servers verify your email’s signature, confirming its authenticity.
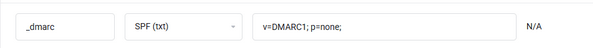
DMARC Setup:
- Create a DMARC policy with a TXT record in your DNS.
- Example:
Host: _dmarc
Record Type: TXT
Address: v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; - Start with p=none to monitor authenticated vs. unauthenticated emails via DMARC reports. Once you’re confident, consider p=quarantine or p=reject for stronger protection.
- DMARC reports help you track all email activity across your domain and sub-domains, ensuring nothing slips through the cracks.
You can update these records through your domain registrar’s DNS panel or KartHost’s Customer Center, where you’ll find the exact records needed.
FAQ: Common Questions About SPF, DKIM, and DMARC
Q: Do I need DMARC if I only forward emails and don’t send them?
A: Yes. DMARC protects your domain from spoofing and ensures forwarded emails aren’t marked as spam, especially if you forward to Gmail, Yahoo, or Outlook. For more information on DMARC and Email Forwarding, please visit our knowledge page specialized for this topic at Domain Names using Email Forwarding SPF, DKIM, DMARC Requirements - KartHost LLC.
Q: What happens if I send over 5,000 emails daily without DMARC?
A: Major providers like Google, Yahoo, and Microsoft may flag your emails as spam or reject them, reducing your deliverability and potentially harming your domain’s reputation.
Q: How do DMARC reports help me?
A: DMARC reports, sent to the email address in your DMARC record (e.g., dmarc-reports@yourdomain.com), show which emails from your domain and sub-domains pass or fail authentication. This helps you spot unauthorized senders or configuration issues.
Q: Why use p=none for DMARC?
A: p=none lets you monitor email activity without affecting delivery. It’s ideal for testing, as it shows which emails are authenticated and which aren’t, helping you fine-tune your setup.
Q: My forwarded emails are going to spam. What’s wrong?
A: Your SPF record may not include the forwarding server, or your DMARC policy might be too strict. Update SPF to include the forwarding server and set DMARC to p=none while monitoring reports.
Q: How do I check if my SPF, DKIM, and DMARC are set up correctly?
A: Use free tools like MXToolbox or DMARC Analyzer to test your DNS records. DMARC reports also provide ongoing insights into your email performance.



























